- Prologue
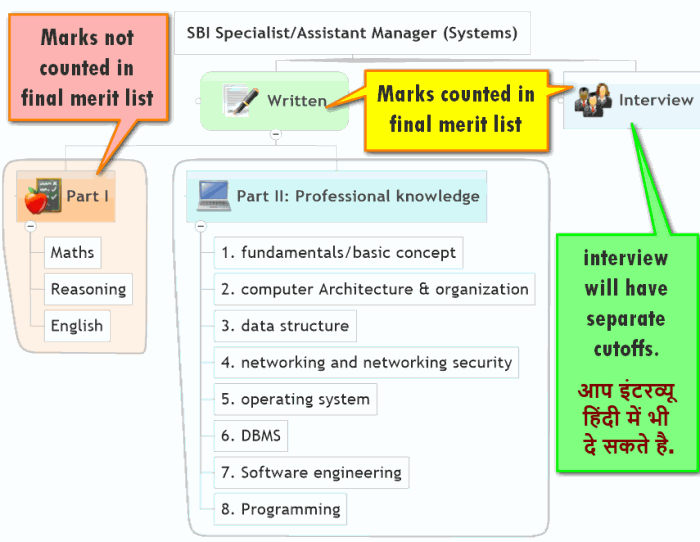
- SBI Specialist: Written stage
- Part II professional knowledge (PK): Systems/IT
- SBI IT (Systems) Assistant Manager 2012 Question Paper
- SBI Specialist (Computer & Communication) 2012 Question Paper
- IBPS specialist Question paper 2012 and 2013 Exam
Prologue
- State bank of India (SBI) recently notified vacancies in specialist officer cadre.
- Some readers had been requesting the question papers. So here it is.
SBI Specialist: Written stage
DONOT waste time in GA/GK, Banking, current affairs and Marketing = because they’re not part of the exam.
| Part I | Maths, reasoning, English | score not counted in merit list, but you need to cross minimum cutoff. |
| Part II | Professional knowledge (PK) | score counted in merit list. |
Part I: Maths, English, Reasoning: How to approach?
- Its marks not counting in final merit list. But you’ve to cross cutoffs, otherwise your part II will not be evaluated.
- In other words, this is same like UPSC’s compulsory English language paper in Mains exam).
- Since its marks are not counted in merit list. You only need to cross the cutoff. Therefore, I don’t recommend separate books on maths/reasoning/English for this exam. You don’t need to “master” these topics. Just practice enough questions so you can tick 15-20 MCQs in each section and move on to part II (professional knowledge).
- For this, solve previous PO papers. [You don’t need ‘special’ papers for specialist officer- the routine PO papers also work fine- as far as maths, english, reasoning is concerned.
- Besides, whatever “mock” tests/ books are in the market, their MCQs are usually jugaad-lifted from previous PO exam papers.
- You don’t even need “brand new” paperset- pick whatever second hand/used paperset you can get from the local book-bazaar. In the Bank paperset market, three noted publication houses are: Arihant, Disha and Kiran publication. (Use anyone- whichever you can get cheap.)
- Even in those papersets, don’t waste time practicing everything. Just focus on following areas:
High priority areas in Part I (Maths, English, Reasoning)
| REASONING |
These questions usually come in a set of 3-5 MCQs =12-20 MCQs are done. |
| MATHS |
IGNORE: Trigonometry, quadratic equations, logarithms, coordinate geometry. Because they don’t ask it in SBI. So don’t waste time in those topics. |
| ENGLISH |
|
- If you master above areas, then crossing the cutoffs in Part 1 should not pose big challenge.
- In the real-exam, DONOT waste time in solving 1,2,4… all MCQs in a linear fashion. I can’t predict cutoffs. But to be on safe side, at least 15 should be ticked in each section accurately before moving to next section. If time permits even after doing everything else, then tick more in the second round.
- In Bank exams, often sincere players fail, because they spent too much time in the English portion. Since English is relatively easy- so these people try to solve all English MCQs, before moving to next section. Avoid this stupid mistake.
Part II professional knowledge (PK): Systems/IT
- Total 50 questions.
- Its marks counted in final merit list. (Along with interview marks).
- Therefore, you must give highest priority to this area.
SBI Specialist Syllabus for System/IT/ Professional knowledge topic
As such SBI notification doesn’t give detailed syllabus. But if you observe the index of recently launched books, you can get a rough idea about what topics should be prepared (from your college books/GATE guidebooks/internet.) for example:
| Disha publication book index says | Kiran Prakshan book index says |
|
|
From the indexes of these two books, you can see following topics are common
- fundamentals/basic concept
- computer Architecture and organization
- data structure
- networking and networking security
- operating system
- DBMS
- Software engineering
- Disha says programming, Kiran says “C programming”.
So first dig those common topics from whatever college textbooks/GATE guidebooks you’ve.Or through internet. I’ve also included the previous papers of SBI PO exam (professional knowledge section) below. Use them to get a better idea on what areas are to be covered- what is the depth and difficultly level of the papers.
Beyond that, I cannot say much because I’m a Pharmacist and not an IT graduate. If any senior player/ maestro wants to share more wisdom about the PK section- please post it under the comments.
SBI IT (Systems) Assistant Manager 2012 Question Paper
Question 1 to 25
- In SQL, which of the following is not a data Manipulation Language Commands?
- Delete
- Select
- Update
- Create
- None of the above
- The value for an attribute or a column are drawn from a set of values known as –
- Tuples
- Attributes
- Domain
- Column
- None of these
- Entities having primary key are called
- Primary Key
- Strong entities
- Weak entities
- Primary Key
- None Of these
- Which of the following is not a type of SQL statement?
- Data Manipulation Language (DML)
- Data Definition Language (DDL)
- Data Control Language (DCL)
- Data Communication Language (DCL)
- None of these
- Which of the following is not included in DML (Data Manipulation Language)
- INSERT
- UPDATE
- DELETE
- CREATE
- None of these
- TRUNCATE statement in SQL is a –
- DML statement
- DDL statement
- DCL statement
- DSL statement
- None of these
- To discard all pending data changes
- COMMIT
- ROLLBACK
- SAVEPOINT
- LOCK
- None of these
- Which of the following term is related to the stack?
- TOP
- PUSH
- POP
- Rear
- A, B and C.
- In Queues, the end from where items inserted is called
- Rear
- Front
- Top
- Base
- None of these
- Which protocol is used for browsing website:
- TCP
- FITFP
- FTP
- TFTP
- None of these
- Which of the following is a browser?
- Netscape Navigator
- Mosaic
- Mozilla Firefox
- Google chrome
- All of these
- Black Box Testing sometime called –
- Data flow testing
- Loop testing
- Behavioral testing
- Graph based testing
- None of these
- The Objective of testing is
- Debugging
- To uncover errors
- To gain modularity
- To analyze system
- None of these
- Choose the right sequence of SDLC (Software development life cycle) steps
- Design, Requirement Analysis, Coding, Testing
- Requirement Analysis, Design, Coding, Testing
- Requirement Analysis, Design, Testing, Coding
- Requirement Analysis, Coding, Design, Testing
- None of these
- The drawback of the binary tree sort are remedied by the
- Linear Sort
- Quick Sort
- Heap Sort
- Insertion Sort
- All of these
- Round robin scheduling is essentially the preemptive version of
- FIFO
- Shortest job first
- Shortest remaining
- Longest time first
- None of these
- ____ is the situation in which a process is waiting on another process, which is also waiting on another process which is waiting on the first process. None of the processes involved in this circular wait are making progress.
- Deadlock
- Starvation
- Dormant
- All of these
- None of these
- Assembly language is a _____
- Low Level Language
- Middle Level Language
- High level Language
- User Language
- None of these
- Which of the following is a type of translator?
- Assembler
- Compiler
- Interpreter
- All of the Above
- None of these
- Multiprogramming systems ___
- Are easier to develop than single programming
- Execute each job faster
- Execute more jobs in the same time
- Are used only on large main frame computers
- None of these
- The mechanism by which the data and functions are bound together with an
- Inheritance
- Encapsulation
- Abstraction
- Polymorphism
- None of these
- The OSI model consists of ___layers.
- Nine
- Eight
- Seven
- Five
- Eleven
- Decryption & Encryption of data are the responsibility of the ___ layer.
- Physical
- Data link
- Presentation
- Session
- Application
- LANs can be connected by devices called ____ which operate in the data link layer?
- Hub
- Bridges
- HDLC
- Tunnel
- None of these
- In a ____ topology, if there are n devices in a network, each device has n-1 ports for cable.
- Mesh
- Star
- Bus
- Ring
- None of these
Question 26 to 50
- OLAP applications are widely used by ____ and it uses ____ Schema.
- RDBMS , Bus
- Operating System ,Star
- Java , Bus
- Data mining Techniques; Star or multidimensional
- None of these
- Arrange the following in increasing order of their size.
- Database<File<Record<Field<Byte<Bit
- Bit<Byte<Field<Record<File<Database
- Bit>Byte>Record>Field>File>Database
- Bit>Byte>File>Record>Field>Database
- JVM is a virtual machine that can execute ___
- C language
- .net programming
- RDBMS
- C++ Language
- Java byte Code
- ODBC is based on ___.
- Structured Query Language.
- C language
- C++ language
- .net
- None of these
- Which of the following is not an advantage of the data-base approach?
- Increased security
- Elimination data redundancy
- Ability to associate related data ‘
- Programming/data independence
- All of the above
- In relational database row and column is called as ____and ____respectively.
- Tuple; Attribute
- Attribute; Tuple
- Tupple;Domain
- Attribute; Domain
- None of these
- To delete a particular column in a relation the command used is:
- DELETE
- UPDATE
- DROP
- ALTER
- None of these
- A primary key if combined with a foreign key creates
- Parent-Child relationship between the tables that connect them.
- Many to many relationship between the tables that connect them.
- Network model between the tables that connect them.
- All of the above
- None of the above
- Which of the following is record based logical model?
- Network Model
- Object oriented model
- E-R Model
- All of these
- None of these
- The full form of DDL is
- Dynamic Data Language
- Detailed Data Language
- Data Definition Language
- Data Derivation Language
- All of these
- Which of the following virus overtake computer system when it boots and destroy in-formation?
- Trojan
- System infectors
- Boot infectors
- Stealth virus
- None of these
- The relational model includes two general integrity rules. Integrity rule 1 is concerned with ____ and integrity rule 2 is concerned with ____
- Primary Key, Foreign key
- Primary Key, composite key
- Unique key, Foreign key
- Composite Key, Foreign key
- None of these
- ____ is person who has the central control over both data and application programs.
- System engineer
- Database administrator
- Database manager
- Technical analyst
- None of these
- An attribute of a relation that references the primary key of another relation is known as the ____
- Foreign Key
- Unique Key
- Parent key
- Child key
- Index key
- An entity set that does not have sufficient attributes to form a primary key is a
- strong entity set
- weak entity set
- simple entity set
- primary entity set.
- None of these
- The JDBC-ODBC bridge is
- Three tiered
- Multithread
- Best for any platform
- All of these
- None of these
- In a relational database, this is a data structure that organizes the information about a single topic into row and columns.
- Block
- Record
- Tuple
- Table
- None of these
- Which statements about the Java language are true?
- Java supports both procedural and object-oriented programming
- Java is only a procedural language.
- Java is only an Object-Oriented.
- Java is related to
- None of the above.
- Stack is also called ____
- First In First Out (LIFO)
- Last In First Out (FIFO)
- First In Last Out (FILO)
- First Come First Served (FCFS)
- None of the above
- The index created by primary key column is called _____
- Unique Index
- Composite Index
- Single Index
- Primary index
- None of these
- In SQL ,which command(s) is(are) used to remove rows from a table.
- Delete
- Remove
- Truncate
- Both
- and (3)
- None of the above
- In SQL, the CREATE TABLE is used
- To create a table, defining its columns, integrity constraints, and storage allocation
- To add a column/integrity constraint to a table.
- To redefine a column
- To change a table’s storage characteristics
- All of the above
- What is the abbreviation is used for a software package that permits the user to create , retrieve and maintain records in a database?
- DASD
- CRMD
- DBMS
- All of these
- None of the above
- Choose the right sequence of virus stages –
- Triggering, Damage ,Dormancy, propagation
- Damage, Triggering ,Dormancy, propagation
- Damage, Triggering, propagation ,Dormancy
- Triggering, Damage, propagation, Dormancy
- Dormancy, Propagation,. Triggering, Damage
- In SQL, which command is used to add new rows to a table?
- Alter Table
- Add row
- Insert
- Append
- None of the Above
SBI Specialist (Computer & Communication) 2012 Question Paper
Q1 to 25
- To create a copy files in the event of system failure, you create a ___
- Firewall
- Redundancy
- Backup
- Restore file
- None of these
- Print server uses___ which is a buffler that holds before it is send to the printer.
- Queue
- Spool
- Node
- Stack
- None of these
- Which of the following identifies specific web page and its computer on the web page?
- Web site
- URL
- Web site address
- Domain Name
- None of these
- _____ is the computer to computer exchange of routine business data between trading partners in standard data formats.
- CTS
- DSR
- VDR
- EDI (Electronic data interchange)
- None of these
- Communication handler is basically an ____ 16 bit micro controller?
- 8085
- 8086
- 8086A
- 80C186
- None of these
- Which uses a Pre-Shared Key that is more than 7 and less than 64 characters in length?
- WPA-PSK
- TKIP
- AES
- All of these
- None of these
- Ping command is used for what purpose?
- Test a device on a network whether it is reachable
- Test a hard disk fault
- Test a bug in the application
- Test devices scanning quality
- None of these
- Two different kind of networks can be connected by using—
- Bridges
- Satellite
- Gateway
- Routers
- None of these
- Full adder is used to—
- 2 bit addition
- 3 bit addition
- 4 bit addition
- 6 bit addition
- None of these
- Most important advantage of an IC is its—
- Easy replacement in case of circuit failure
- Low power consumption
- Extremely high reliability
- Reduced cost
- None of these
- An 1C contains 50 gates each of which consists of 6 components. Its belongs to
- VLSI
- LSI
- MS1
- SSI
- None of these
- Which type of computers use the 8 bit code called EBCDIC?
- Minicomputers
- Mainframe computers
- Super computer
- Microcomputer
- None of these
- An AND gate
- Implements logic addition
- Is equivalent to a series switching circuit
- Is any-or all gate
- Is equivalent to a parallel switching circuit
- None of these
- The decimal equivalent of the binary number 11100001111 is
- 1806
- 1807
- 2806
- All of these
- None of these
- Programs in which of the following memories can’t be erased ?
- RAM
- ROM
- Cache Memory
- Virtual Memory
- None of these
- The IP address 135.0.10.27 belongs to address class?
- A
- B
- C
- D
- None of these
- Which are not used in case of applet?
- Read /write
- Internet
- Search engine
- All of these
- None of these
- Which of the following is not a type of database?
- Hierarchical
- Relational
- Network
- Transition
- None of these
- Which of the following is not a type of SQL statement?
- Data Manipulation Language
- Data Definition language
- Data control language
- Data Standard language
- None of these
- In Queue , the items deleted at one end is called
- Rear
- Front
- Top
- Base
- None of these
- The drawback of the binary tree sort are remedied by the
- Linear sort
- Heap Sort
- Insertion sort
- Quick Sort
- None of these
- White Box testing, a software testing technique is sometimes called
- Graph testing
- Basis path
- Glass box testing
- Data flow testing
- Loop testing
- Which of the following is used with database?
- EDI
- Credit card
- ATM
- Payment gateway
- Data mining
- When a cracker attempts to misuse or steal data from a system, it is called
- Stealing
- Intrusion
- Virus
- Worm
- None of these
- To modify existing rows of the table ____ statement is used.
- ALTER
- MODIFY
- UPDATE
- COMMIT
- DELETE
Q26 to 50
- ____ refers to a family of IEEE standards dealing with local area network and metropolitan area network.
- 802
- 800
- 801
- 803
- None of these
- Which is the general network standard for the data link layer in the OSI Reference Model?
- IEEE 802.1
- IEEE 802.2
- IEEE 802.3
- IEEE 802.4
- IEEE 802.6
- ____ uses a standard called IEEE 802.6.
- LAN
- WAN
- MAN
- Internet
- None of these
- Repeater operates in which layer of OSI model?
- Application layer
- Presentation layer
- Physical layer
- Transport layer
- Data link layer
- Where does Bridge operate in OSI model?
- Physical layer
- Data link layer
- Both (1)and (2)
- Application layer
- None of these
- Which of the following uses the greatest number of layers in the OSI model?
- Bridge
- Repeater
- Router
- Gateway
- None of these
- Routers operate in which layer of the OSI model?
- Physical layer
- Data link layer
- Network Layer
- All of these
- None of these
- Modem is a _____ that modulates and demodulate signals
- DCE (Data circuit-terminating equipment)
- DTE (Data terminal equipment)
- DTE-DCE
- Both (1)and (2)
- None of these
- A communication network which is used by large organizations over regional, national or global area is called ___
- LAN
- WAN
- MAN
- Internet
- None of these
- At ___ layer, TCP/IP defines two protocols :Transmission Control Protocol (TCP) and User Datagram Protocol(UDP).
- Transport layer
- Network layer
- Physical layer
- Application layer
- None of these
- The ___ layer is the layer closest to transmission medium.
- Transport
- Network
- Data link
- Physical
- None of the above
- End to end connectivity is provided from host to host in :
- Network layer
- Session layer
- Data link layer
- Transport layer
- None of these
- Which of the following TCP/ IP protocol is used for transferring electronic mail messages from one machine to another?
- SNMP
- SMTP
- RPC
- FTP
- None of these
- Which of the following is an example of a client-server model?
- FTP
- DNS
- TELNET
- All of these
- None of these
- Which IEEE Standards is usz for Wi/Fi systems?
- 802.11
- 802.1
- 802.2
- 802.3
- 802.10
- _____ is the continuous ability to send and receive data between interconnected networks.
- FTP
- SMTP
- TNS
- Network Interoperability
- None of these
- What is the default subnet mask for a class B network?
- 127.0.0.1
- 2550.0.0
- 255.255.0.0
- 255.255.255.0
- None of these
- What is loopback address?
- 127.0.0.1
- 255.0.0.0
- 255.255.0.0
- 127.0.0.0
- None of these
- Internet-like networks within enterprises.
- Intranets
- Switching alternating
- Inter organizational networks
- Extranets
- None of these
- A central computer surrounded by one or more satellite computers is called a
- Bus network
- Ring network
- Star network
- All of the above
- None of these
- With an IP address of 100,you currently have 80 subnets.What subnet mask should you use to maximize the number of available hosts?
- 192
- 240
- 248
- 224
- 252
- Encryption/decryption provides a network with____
- Privacy
- Authenticity
- Integrity
- Non-reputation
- None of these
- The data to be encrypted at the sender site is called ___.The data to be decrypted at receiver end is called ____
- Secret key, public key
- Public key, secret key
- Plaintext, ciphertext
- Ciphertext, plaintext
- None of these
- In digital signature the private key is used for ___ and the public key for ____
- Encryption, decryption
- Decryption, encryption
- Plaintext, ciphertext
- Ciphertext, plaintext
- None of these
- A ___ ‘s main purpose is to prohibit unauthorized access to your computer via the Internet.
- Popup blocker
- Firewall
- Spyware
- Spam assassin
- None of these
IBPS specialist Question paper 2012 and 2013 Exam
Already given. Click me
For entire Archive of all IBPS/Banking related articles, visit Mrunal.org/IBPS
If any senior player/ maestro wants to share wisdom- please post it under the comments.

![[United India AO] Share your Mains exam experience for benefit of future aspirants](https://mrunal.org/wp-content/uploads/2014/12/Cover-United-AO-500x383.jpg)
![[Result] IBPS PO 2014 result out for written exam + call letters for clerks, Marksheets for RRB](https://mrunal.org/wp-content/uploads/2014/11/Cover-result-ibps-po-2014-500x383.gif)
Sir,
i have applied for the post of asst manager(system) and it will be pleasure if you ll send me previous papers of part-II..
can i have answers to this questions
Does only Professional Knowledge sections accounts for final merit in Law Officer IBPS also along with the one described by you?
could u send me part key?
send me part 2 key???
Dear Sir/Mam,
I need the answer of the above questions to check myself how far I am right.
So may please give a link to check the answers.
thanking you.
#So may you please….
give me sollution of part-2 paper of sbi sp officer
please provide answers to the above questions and suggest a book for preparing particularly the pk section
Plz send me some question paper plz it’s very urgent…
sir please provide us the preparation strategy for the upcoming SBI PO exam. we are waiting for that.
Sir,
Is their is negative marking in the SBI SO Exam…??
yes. for every wrong answer 0.25 of marks will be deducted from your score. So it’s always better to leave those questions you’re not sure & attempt only when you’re confident.
Plz sir send me other practice paper of PK…plz sir….
Plz sir send me other practice paper with solution of PK…plz sir….
Plz it’s urgent
Hi sir I want previous question paper of sbi so it off.with answer and model paper for pracitce with answer.
Hi sir I want previous question paper of sbi so it off.with answer and model paper for practice with answer.
is there is negative marking in sbi specialist exam?
hello guys.. Plan well before appearing in the exam. It becomes easy if you plan how to distribute the time for solving each sections. Dont waste too much time on a single section. Focus more on the IT .. thats the fate changer.. good luck.
Plz provide answers for the given questions
which helps in preparation.
sir pls send me previous paper for the post of asst manager (system).
Thanks for the SBI (Systems) paper sir.. Please provide the key if anyone have.. my email id is shiraj.146@gmail.com
Thank you..
Please send answer of above question and also send practise paper
Howdy Hope you may be fine, Since it is not mentioned in the advertisement , So Stay Guarded :)
Sir u r nt replied ….plz help me….answer and practices paper of PK…and is there negative Marking
Plz give the solution for that
thanks for the valuable info
In advertise nt mention negative marking…..tell me exact
pls send me answers to it …
Can u plz send me answers of all these questions
vry valueble info i get through ur site…
can i get whole paper of previous yr 2 summerrize
plz send me on my id..
thank u
i started reading ur model papers … but it wil be more helpfull if u can provide us with answer
sir ………….plz send me ansr key [ bachhaoratu@gmail.com]